In a recent trip down the rabbit hole, I started evaluating various site security products for some of the wordpress sites that I run or manage. Moral to the story, if you ask questions, you’re going to sign up for more work when you hear the answers, but I guess thats ok….
I had recently switched everything to SSL served, after reading https://fourdots.com/blog/why-you-need-ssl-to-rank-better-in-2016-and-how-to-set-it-2169 , but failed to take note of the SSL settings on my server.
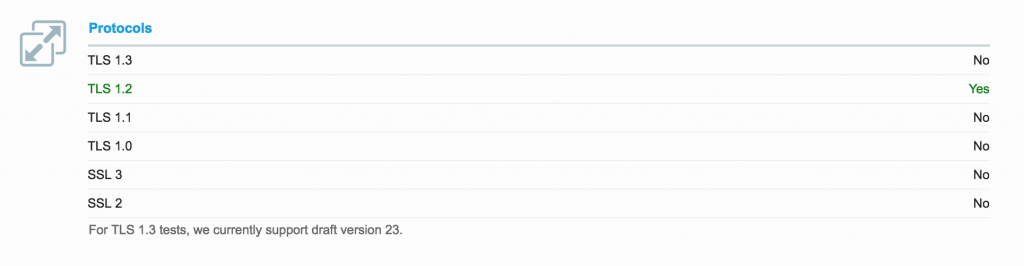
My default settings were “secure” but allowed several technologies that have proven exploits. Largest issues were TLS 1.0 and TLS 1.1, and RC4 Cipher.
This host is a Centos 7.x host, with apache vhosts. Try as I might to edit the SSL settings in the vhost, I still had less than stellar reports.
It seems that apache loads /etc/httpd/conf.d/ssl.conf before the *.vhosts, so whatever is set in that file, ends up being the global setting everyone sticks to.
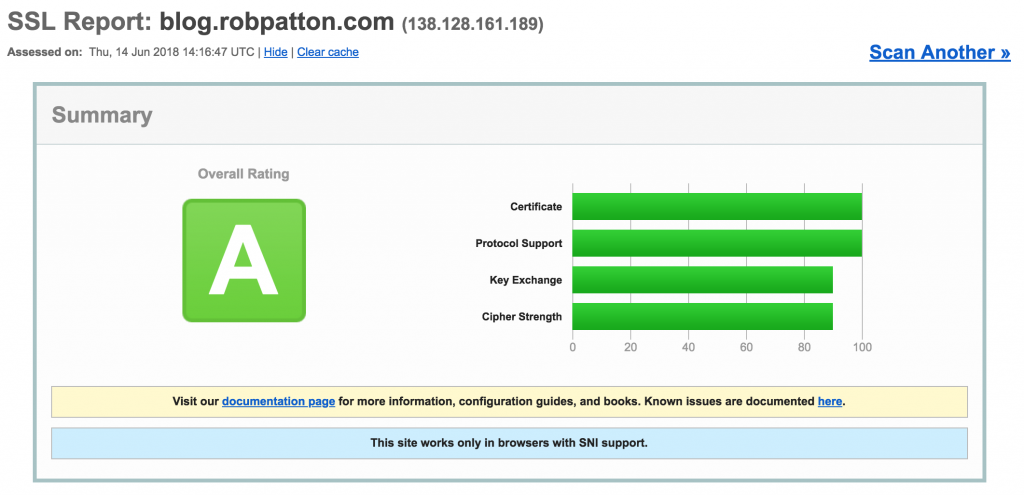
Go test yours! https://www.ssllabs.com/ssltest/index.html
I’m currently using:
SSLProtocol TLSv1.2
SSLCipherSuite HIGH:MEDIUM:!aNULL:!MD5:!SEED:!IDEA:!RC4
as my settings in the file, and the security scans now seem to be A/95%, which was my goal, I guess